Get This Report on Sharepoint Data Migration
This will help you establish cutover dates for all material and individuals and resolve any kind of threats you've determined, such as sites or data shares that require to be rubbed, lawful hold or e, Exploration problems, or perhaps holidays or other essential company days or events that you require to consider.
Your company may like to have users in some service units manually relocate their web content to One, Drive or Share, Direct from share network documents or various other sharing apps, while various other organization devices with numerous TBs of consumer content or sensitive IP may favor that IT and safety teams function with each other to move material to its new place.
You can ask individuals to manually submit their data to Share, Point or One, Drive. This works best for smaller files like general Word papers, Excel spread sheets, as well as Power, Point presentations. Moving little private apply for private customers who have a great deal of material to relocate, they can mount the One, Drive Sync App for Windows or Mac to drag and also go down documents from documents shares or their computer's File Traveler to One, Drive.
All about Sharepoint Data Migration
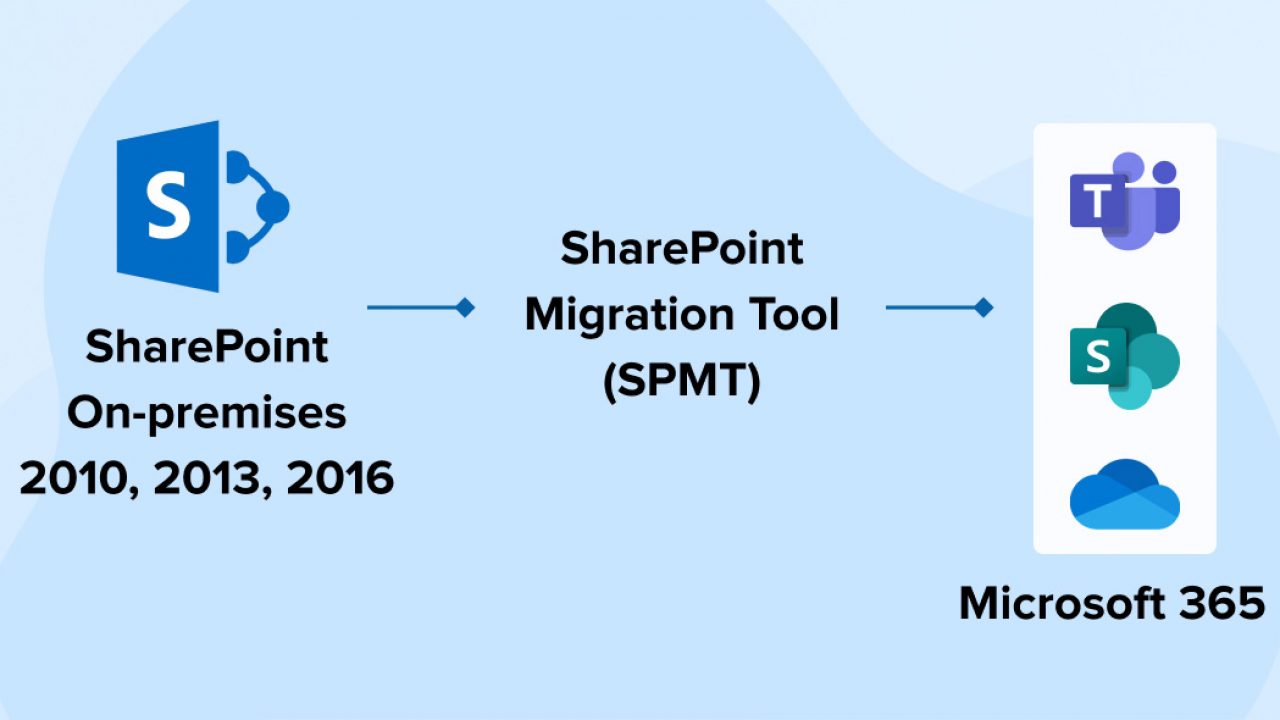
Moving an individual data library to the cloud You can make use of the Share, Point Migration Device (SPMT) to migrate your data from Share, Point on-premises record libraries, listings, or routine data shares. You can also use the brand-new Power, Shell cmdlets based on the Share, Factor Movement Device (SPMT) migration engine to move files from Share, Factor 2010 and also Share, Point 2013 on-premises document collections and checklist products, and also data shares to Microsoft 365.
It also consists of the Share, Point Movement Identity Monitoring Tool, that executes identity mapping by scanning Share, Factor, Active Directory Site, as well as Azure Active Directory Site. Examining Share, Point Web Server 2010 as well as 2013 content before movement Available in the Share, Factor Admin facility, Movement Supervisor gives a central way of connecting web servers, creating tasks, and automatically dispersing your movement jobs.
Moving information from other cloud company The Microsoft Azure Data Box is a solution that allows you purchase a device from the Microsoft Azure website (sharepoint data migration). You can then copy TBs of information from your servers to the tool, ship it back to Microsoft, as well as your data is duplicated into Azure.
Eliminating the dependency on your WAN web link to transfer information when migrating data Relying on the device you choose to make use of for your movement and your company's service demands, you may want to plan your migration throughout off-work hrs or on weekend breaks, ideally, just to pop over to this web-site avoid interrupting everyday organization. sharepoint data migration.
Sharepoint Data Migration Things To Know Before You Get This
Whenever as well as nevertheless you make a decision to move content, you ought to also develop an interactions strategy, offering individuals a lot of advanced notice and clarifying what they need to anticipate and also when. If you have a change administration group, you can also function with them on making sure that paperwork and also training materials are readily offered when the movement begins (sharepoint data migration).
An effective pilot can assist build confidence, specifically with management as well as other key stakeholders, and also can aid you mitigate threats. Select individuals from across the organization who own data that they are sharing with each other and/or with external parties so you can test exactly how consents transfer. You can keep your pilot running even during the actual migration just to aid lessen surprises.

The Sharepoint Data Migration Statements
Migrating to Share, Factor Online from on-premises or other systems can be a complicated and tough process, check it out yet it can likewise bring many advantages such as enhanced adaptability, scalability, as well as safety. As a practice supervisor, IT Director or CIO, you are liable for guaranteeing that the movement achieves success, smooth, and also lined up with the company's objectives as well as needs.
Strategy the migration technique: Pick the very best migration method based upon the scope, objectives, and evaluation outcomes, considering variables such as data size, intricacy, and criticality. Prepare the target setting: Ensure that the Share, Point Online setting is correctly set up, optimized, as well as all set to receive the moved information and material.
Map the information and material: Develop a comprehensive map of the information as well as content that you wish to relocate, consisting of the location, structure, partnerships, and metadata. Choose the right tools: Select the ideal tools for the migration, such as Microsoft's Share, Factor Movement Tool, Share, Gateway or Ave, Factor, relying on your particular requirements and also needs.